Stanford University runs a Phishing Awareness Program that aims to train participants in how to recognise, report and avoid phishing attacks. Given that email is the entry point for 91% of cyber attacks and therefore every organisation’s biggest vulnerability, perhaps we can all benefit from increasing our phishing awareness.

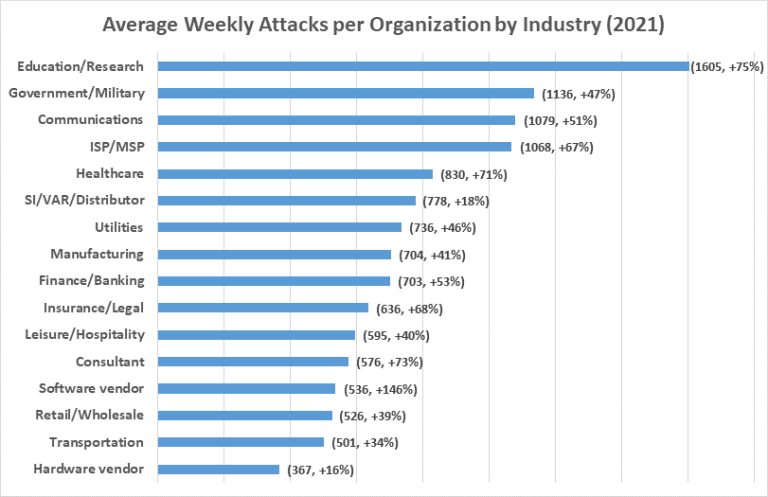
According to Stanford University, 1 in 10 phishing attacks succeed, which is a shockingly high statistic. Even if that probability was only 1%, the danger would remain considerable, given how easy and inexpensive it is to send mass email these days. And according to Check Point Research, “in 2021, there was a 50% increase in overall attacks per week on corporate networks compared to 2020”, with education/research being the sector that experienced the highest volume of attacks, with an average of 1,605 attacks per organisation every week!
The FBI even recently put out a public service announcement on Business Email Compromise/Email Account Compromise (BEC/EAC), which is basically a fancy term for phishing attacks.
What Can We Do? #
As written about previously, cybersecurity is an infinite game, and the surest way to stay in the game is to make your security practices marginally better than the majority of other targets out there. In regards phishing attacks, we can raise awareness by providing education to our organisation’s members and take it so far as to test their understanding and compliance using mock phishing campaigns.
First of all, it’s important to understand and communicate a few key things about phishing attacks:
- What they target.
- Why they work.
- How to recognise them.
- Where to report suspicious activity.
The infographic below is a great example of an illustration that explains the above points in simple terms.

Note that I’m using the term “phishing” loosely, to mean social engineering attacks in which personal information is obtained (stolen) for malicious purposes via email, telephone or other common forms of communication. Specific types of attacks include deceptive phishing (impersonating a legitimate company or person), spear phishing (targeting specific people with personalised emails), whaling (attempting to compromise the email account of a high-ranking executive to authorise fraudulent money transfers), vishing (using voice phone calls instead of email), SMiShing (sending malicious links via SMS or text message) and pharming (leveraging cache poisoning against a DNS), which are explained in this article.

Show by Example #
In addition to educating users on the dangers of phishing attacks, the best way to help users, especially non-technical users, avoid them, is to show them examples of what they should look out for. Here’s one that targets employees of fictional E‑Corp.
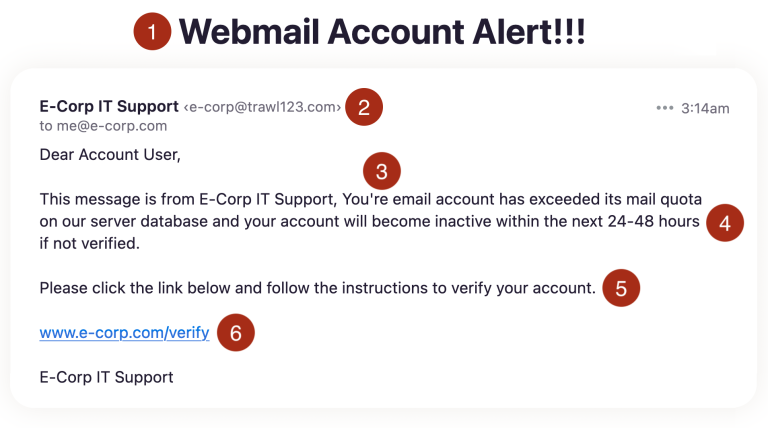
Besides the impersonal touch and unusual wording, it’s easy to imagine how an employee might get jarred by such an email and, in the hopes of getting on on with their busy workday, click the link and proceed to enter their email credentials. This will likely be followed by a pretend confirmation message, along with their credentials being stored by the attacker for malicious use.
Here are the tell-tale signs of a phishing email, as indicated in the image above.
1. Compelling Email Subject #
The email subject may seem compelling, overly urgent or unprofessional. If it sounds like click-bait then this should be considered a red flag.
2. Forged Email Address #
The sender’s name and email address may be forged, even if they look legitimate. It is important to inspect the sending email address and ensure that it matches the signed name in the email body.
3. Incorrect Grammar, Typos #
Incorrect grammar, misspelled words and poorly written sentences may indicate that the email is a phishing attempt.
4. Sense of Urgency and Threat #
Phishing emails typically prompt you to take urgent action, often with a subtle threat if you don’t.
5. Request for Personal Data #
Phishing attacks generally lead you to a page in which your personal data, account information or credentials are requested. Be extremely cautious whenever asked for personal or account information via an email.
6. Disguised or Modified Links #
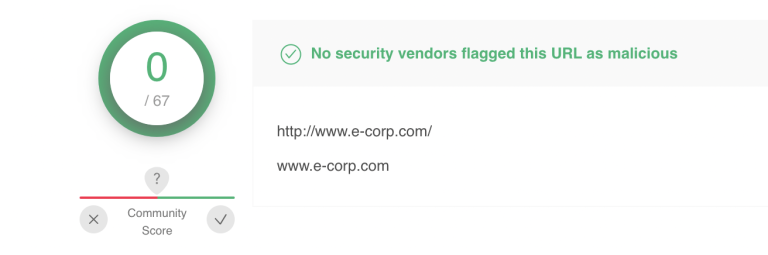
Links in emails can be easily disguised. Even though the link text may display the www.e-corp.com URL, the link URL may be to a completely different, or a similar looking but still different URL. Many email clients show you the actual link URL when you hover your mouse over the link, but some do not. Be sure to check the actual URL before clicking on it, to ensure that you are not being tricked into voluntarily visiting a fraudulent site.
Finally, if you do click a link, ensure that the domain name is genuine. Beware of sneaky typos in domain names, intended to go unnoticed, such as www.e-corp.c2x.com or www.e-corp.cf. If you’re not sure about the URL, use a service such as VirusTotal that allows you to submit a URL and find out whether the URL has been flagged as malicious.
Beware the Attachment #
Receiving unexpected attachments via email should always have you on high alert, especially files of type .exe, .zip, .rar, .doc, .xls, .ppt, etc. but even something as benign as .pdf can contain malware or viruses. The rule of thumb is, if you don’t know and trust the sender and are not expecting the attachment, don’t open it!!
If you know the sender, contact them and to confirm whether they intended to send and attachment and ask what it contains. Alternatively, you can upload the file to VirusTotal and it will tell you whether it contains malware or a virus.
It’ll-never-happen-to-me Syndrome #
One of the biggest challenges is getting users past the belief that they will never actually fall for a phishing email. Anyone can fall for these scams, including the technically inclined!!
If you don’t believe me, take this Phishing Quiz to see just how hard it can be to spot these deceptive scams.

So just like a fire drill, I suggest you send the users in your organisation, or your client’s organisation, a mock phishing email a few weeks or months after training them on the above. Be sure to measure how many people react to the email in the following ways:
- Report the email to the person responsible for security.
- Ignore the email or take no action.
- Click the malicious link.
- Enter their account credentials.
The goal of this exercise is not to shame people, but to give them practice in identifying and reporting, as well as to help sensitise them to, potential attacks.
Email Spoofing #
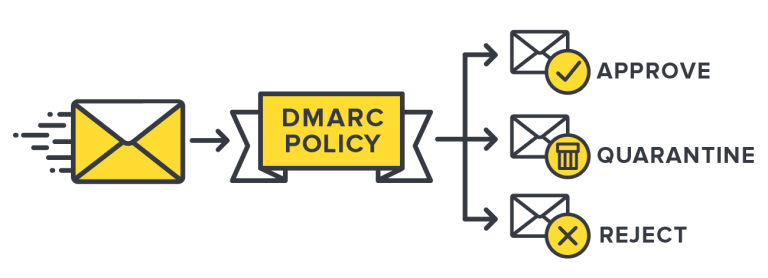
Phishing is hard to prevent, but one thing you can do to help mitigate it is set up DMARC (Domain-based Message Authentication, Reporting & Conformance) for your domain. DMARC is a standard that prevents spammers from using your domain to send email without your permission — also known as email spoofing. For a full explanation of DMARC, as well as DKIM (Domainkeys Identified Mail) and SPF (Sender Policy Framework), refer to this excellent DMARC guide.
Also, Postmark offers free DMARC monitoring that provides you with weekly email reports showing who is sending email from your domain, allowing you to tweak your DKIM and SPF authentication policies as required.